How a Trusted Managed IT Provider Can Support Your Business Remain Competitive and Safe
How a Trusted Managed IT Provider Can Support Your Business Remain Competitive and Safe
Blog Article
Discover the Crucial Kinds Of IT Managed Services for Your Company Needs
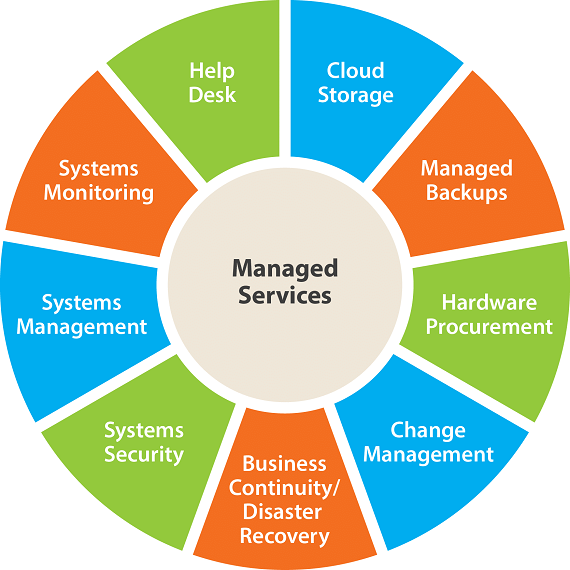
In today's quickly evolving technical landscape, comprehending the important sorts of IT took care of solutions is vital for organizations looking for to enhance performance and safety. From network administration that makes sure smooth connectivity to robust cybersecurity measures made to repel arising dangers, each solution plays an unique duty in strengthening business facilities. Cloud services and proactive IT sustain can substantially impact functional agility. As we explore these solutions additionally, it becomes noticeable that straightening them with specific organization requirements is essential for achieving optimum performance and development. What might this positioning resemble for your organization?
Network Administration Services
Network Administration Provider play a vital role in making sure the security and effectiveness of a company's IT infrastructure, as they include a series of activities developed to monitor, preserve, and maximize network efficiency. These services are important for companies that rely heavily on their networks for everyday procedures, enabling seamless communication and information transfer.
Trick components of Network Administration Provider consist of network monitoring, which tracks performance metrics and determines possible issues before they intensify right into significant issues. Aggressive management makes sure that network sources are utilized efficiently, lessening downtime and improving performance. In addition, configuration management is vital for keeping optimum network setups, permitting for fast changes in response to changing business needs.
Furthermore, safety administration within these solutions focuses on safeguarding the network from cyber dangers, carrying out firewall softwares, breach detection systems, and regular protection audits. This layered approach safeguards delicate information and keeps governing conformity. Reporting and analysis give understandings into network efficiency patterns, directing future infrastructure financial investments. By embracing extensive Network Management Provider, companies can achieve a resilient and durable IT atmosphere that supports their critical goals.
Cloud Computing Solutions
In today's electronic landscape, organizations progressively transform to Cloud Computing Solutions to improve flexibility, scalability, and cost-efficiency in their IT operations. Cloud computer permits companies to accessibility resources and services online, eliminating the requirement for extensive on-premises facilities. This change causes significant cost savings on upkeep, hardware, and energy costs.
There are a number of kinds of cloud solutions available, consisting of Infrastructure as a Service (IaaS), System as a Solution (PaaS), and Software as a Service (SaaS) IaaS supplies virtualized computer sources, enabling organizations to scale their facilities based upon need. PaaS offers a platform for developers to build, test, and deploy applications without handling the underlying equipment. SaaS supplies software applications through the cloud, permitting customers to access them from any kind of device with a net link.
Additionally, cloud options facilitate cooperation amongst teams, as they can share and access details flawlessly from different areas. In addition, cloud companies frequently implement robust backup and disaster recovery services, better securing service continuity. By leveraging Cloud Computing Solutions, companies can not just maximize their IT sources yet also place themselves for technology and growth in an increasingly affordable market.
Cybersecurity Providers
Cybersecurity Services have ended up microsoft azure information protection client being crucial in guarding business information and framework against an ever-evolving landscape of cyber dangers. Enterprise Data Concepts, LLC. As cybercriminals continuously develop more innovative strategies, companies have to apply durable protection procedures to safeguard sensitive details and keep operational stability
These services generally consist of an array of offerings such as danger analysis and administration, intrusion discovery systems, firewall softwares, and endpoint security. Organizations can gain from constant monitoring that determines and reduces the effects of possible threats before they intensify right into serious violations. Additionally, cybersecurity solutions often encompass employee training programs to promote a culture of safety recognition, outfitting team with the expertise to identify phishing efforts and various other destructive tasks.

Information Backup and Recuperation

Data backup involves creating and storing copies of crucial data in protected locations, guaranteeing that organizations can recuperate info swiftly in case of loss - IT solutions. There are numerous back-up techniques offered, including full, step-by-step, and differential back-ups, each offering unique requirements and providing differing healing speeds
Furthermore, companies should consider cloud-based back-up remedies, which give scalability, remote access, and automated procedures, minimizing the concern on internal sources. Applying a detailed healing plan is just as essential; this strategy must detail the steps for restoring information, consisting of testing recovery refines on a regular basis to Read Full Report make sure performance.
IT Support and Helpdesk
Efficient IT sustain and helpdesk services are critical for maintaining operational connection within organizations. These services act as the first line of protection versus technical issues that can interfere with organization features. By providing prompt support, IT support groups make it possible for workers to focus on their core responsibilities instead of coming to grips with technical challenges.
IT sustain includes a range of solutions, including troubleshooting, software program setup, and equipment maintenance. Helpdesk solutions usually entail a specialized team that manages inquiries with numerous channels such as chat, email, or phone. The performance of these services is usually measured by reaction and resolution times, with an emphasis on minimizing downtime and improving customer complete satisfaction.
In addition, a well-structured IT support group advertises aggressive problem identification and resolution, which can protect against minor problems from intensifying right into major interruptions. Several companies choose outsourced helpdesk solutions to take advantage of specialized expertise and 24/7 availability. This tactical method enables organizations to allocate resources effectively while making certain that their technical framework continues to be robust and dependable.
Verdict
To conclude, the assimilation of important IT handled services, including network management, cloud computing, cybersecurity, information back-up and recuperation, and IT assistance, significantly improves organizational efficiency and security. IT solutions. These services not just address specific organization needs however additionally add to overall operational continuity and growth. By tactically leveraging these offerings, companies can optimize their technological facilities, secure essential information, and make certain punctual resolution of technical issues, ultimately driving productivity and fostering a competitive advantage in the market
In today's swiftly advancing technological landscape, understanding the crucial types of IT took care of services is essential for services seeking to improve efficiency and protection. As we explore these solutions further, it comes to be evident that straightening them with specific service needs is important for achieving ideal efficiency and growth. Cloud computing allows companies to accessibility resources and services over great post to read the net, eliminating the requirement for considerable on-premises facilities.There are several types of cloud services readily available, including Facilities as a Solution (IaaS), System as a Service (PaaS), and Software Application as a Service (SaaS) These services not just address details business requirements yet additionally contribute to general functional connection and development.
Report this page